Booz Allen’s DarkLabs Threat Hunt team developed an advanced technique that pivots on open source indicators of compromise (IOC) to discover new variants of Malware. The life cycle of an openly reported IOC does not end when an operator deploys the indicator to a sensor or a threat hunter checks their security information and event manager (SIEM). Merging the IOC with internal or external raw sources of cyber threat intelligence reveals additional IOCs and malware variants. Additional indicators, robust detection, and advanced analytics can work together to stop threat actors in their tracks. Booz Allen's DarkLabs Threat Hunt team exercised a combination of open-source reporting and acquired sources of threat intelligence, then merged this information with our own internally developed tools to expand and perform deep analysis on previously reported APT34 behaviors.
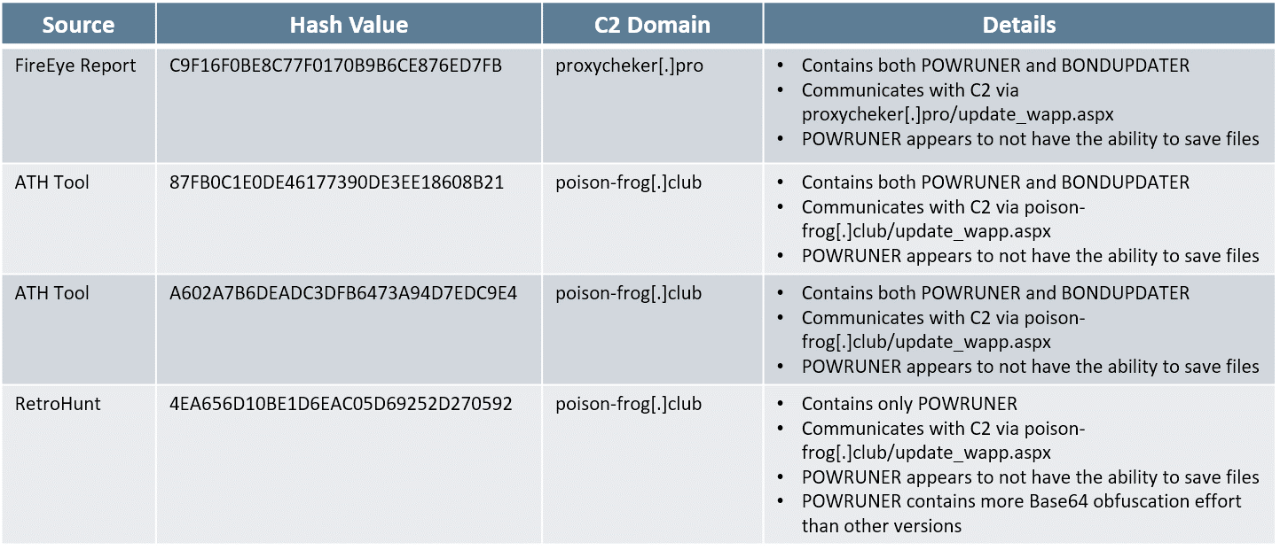
In early December 2017, FireEye released a report discussing recent activity, which they attributed to APT34. APT34 is a group that is thought to be involved in nation state cyber espionage since at least 2014. The FireEye report references binary (MD5: C9F16F0BE8C77F0170B6CE876ED7FB) which is a loader for both BONDUPDATER, the downloader, and POWRUNER, the backdoor. This loader connects to a known Command and Control (C2) domain, proxycheker[.]pro. Using this binary as a starting point, our DarkLabs team of Threat Hunters discovered three additional binaries that appear to be associated with APT34 activity.