Cyber risk has a way of cascading within and across organizations. These risks defy geographic boundaries and blur the seams between industries. Now, with the quantum threat to encryption, certain cyber attacks may cause even greater harm. Cyber risk is not only accelerating across the economy–it’s also accumulating over time. Emerging quantum technologies require you to think differently about cyber risk. Federal agencies and businesses must understand how quantum introduces significant—and sometimes permanent—new risks.
Quantum computers use quantum mechanics to create new pathways through difficult problems. Some say quantum computers are “faster” than classical computers, but that can make it easy to miss what’s really happening. Quantum computers will dramatically accelerate certain calculations, but it isn’t because they perform mathematical operations faster. Rather, the speed-up comes from using mathematical operations beyond the reach of today’s computers. This shift introduces opportunities for innovation and unprecedented threats. Elsewhere, we’ve discussed quantum’s potential to improve positioning, navigation, and timing, financial optimization, healthcare diagnostics and treatment, and more.
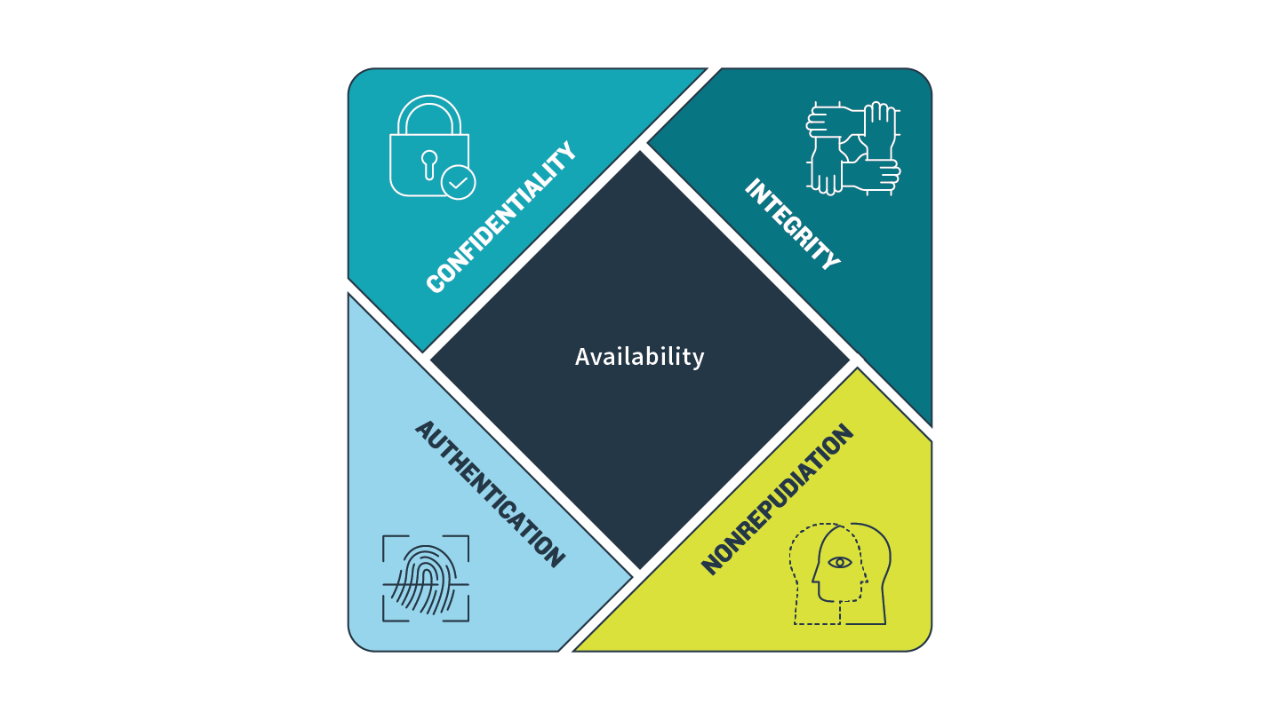
This article focuses on the threat: Quantum computers are capable of breaking modern cryptography, thus compromising sensitive data and communications.