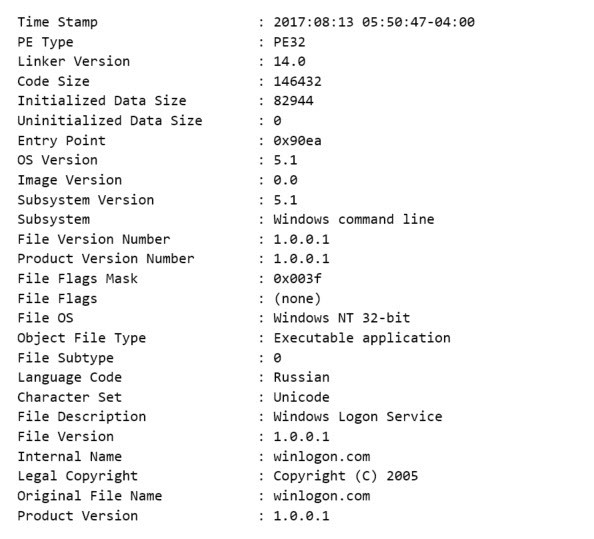
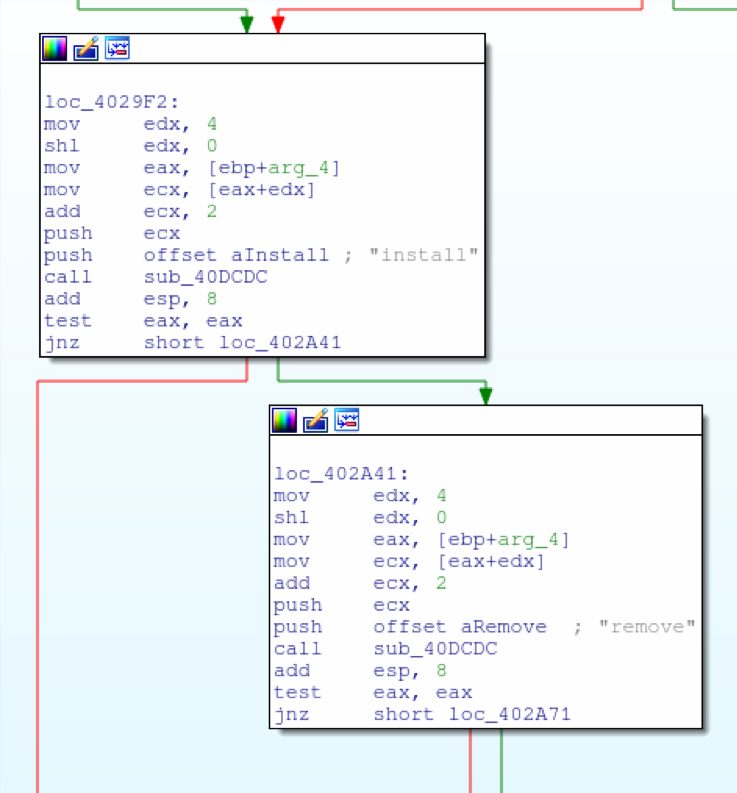
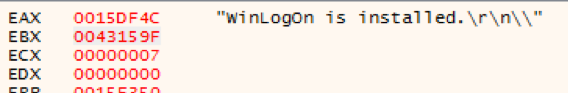
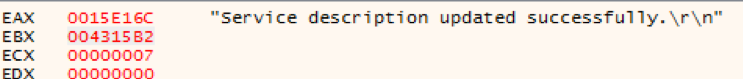
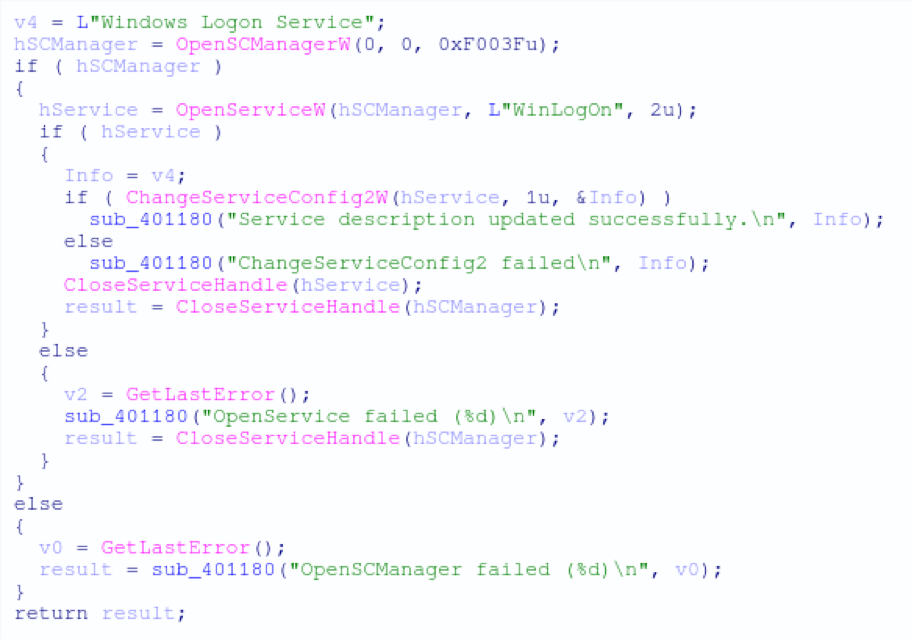
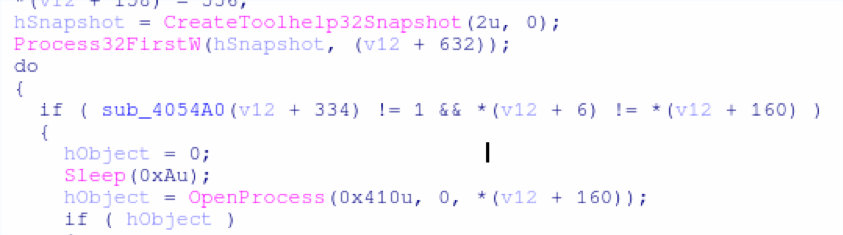
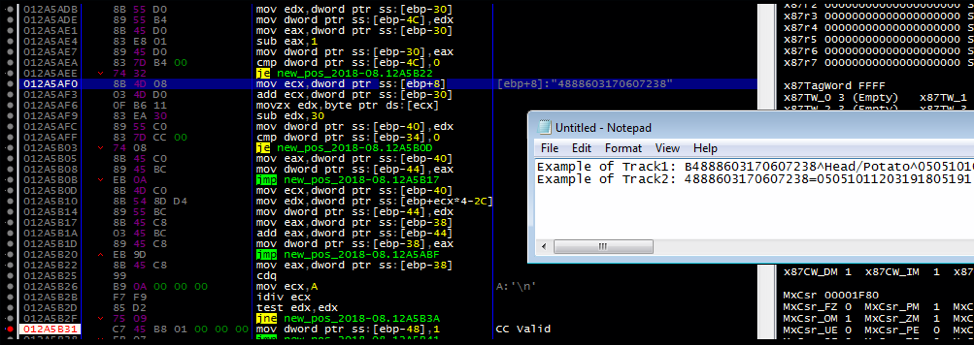
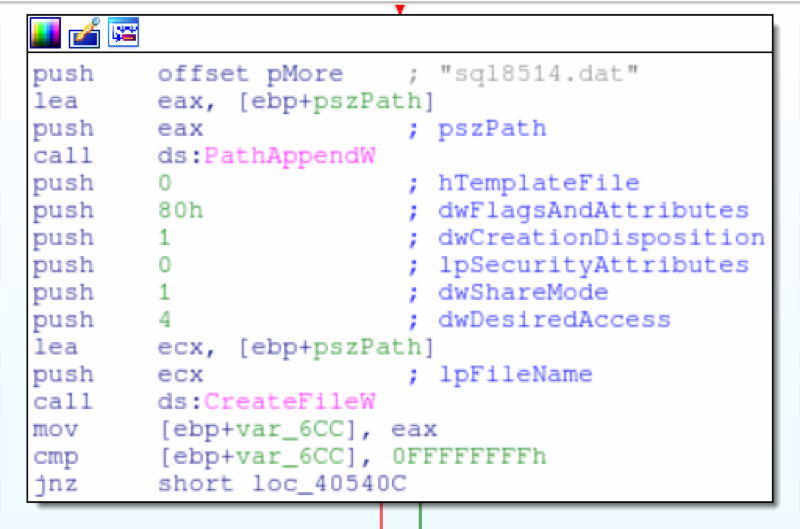
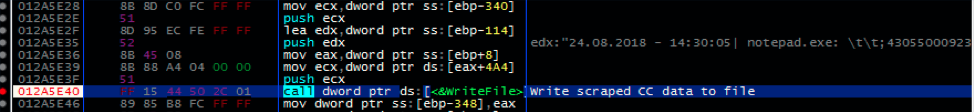
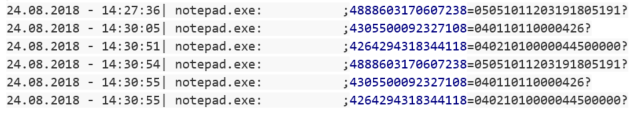
RtPOS is unique in comparison to other fully featured POS malware like Project Hook and TreasureHunter, in that it has no native exfiltration capability. While other POS malware families are perfectly capable of sending captured Track1 and Track2 data to a C2 server, RtPOS merely saves the data locally. As this activity is similar to some POS utilities, this is likely intended to reduce the network activity footprint of RtPOS and ensure the malware remains undetected for longer, thus earning the controllers a healthier profit. The RtPOS malware is also simplistic in features, largely automated in operation, and lacks many of the features that more mature POS malware families do.
The lack of a network exfiltration feature, interaction and user commands, as well as a dropper component hints at more serious implications: in order for RtPOS to execute and in order to retrieve the captured payment card data, the attackers would have existing access to the victim’s machine(s). RtPOS may simply be an in-development POS malware family, though review and analysis suggests RtPOS is a post-compromise tool instead of a standalone malware, and may even be part of a larger, heretofore unidentified tool set.
We offer these recommendations for informational use only and do not make any warranties or other promises they will be effective against the threats described herein.