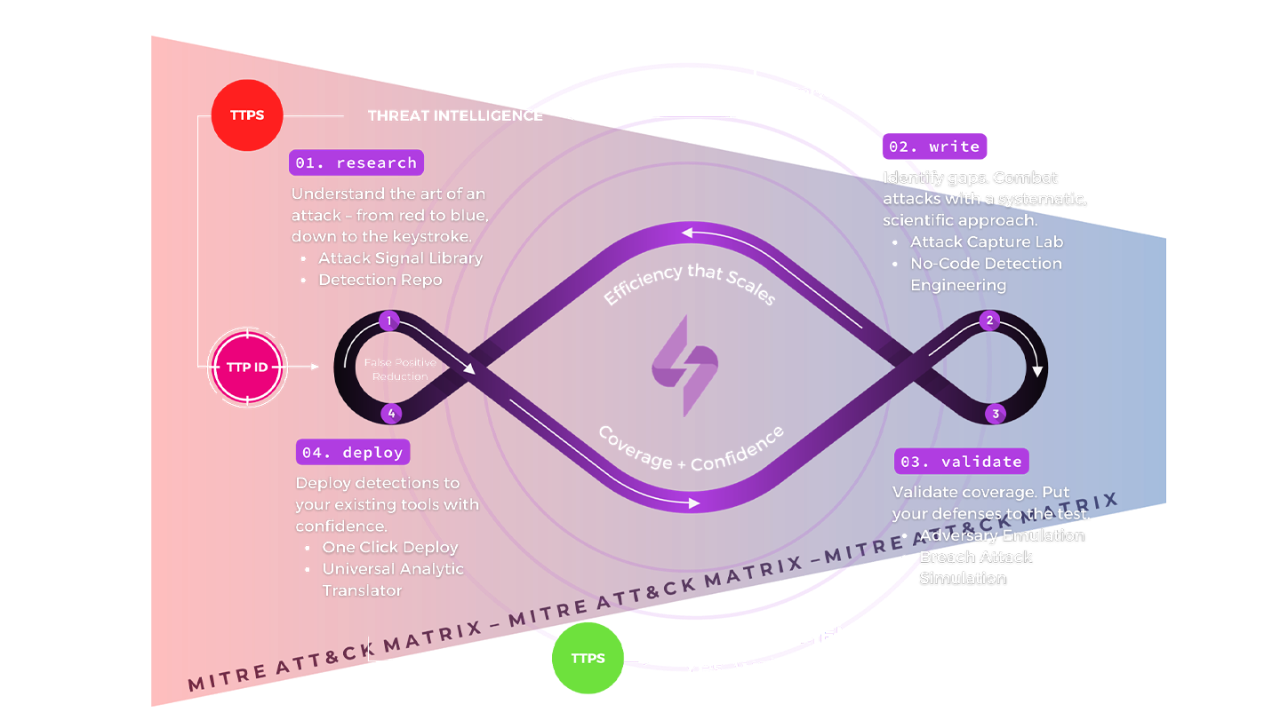
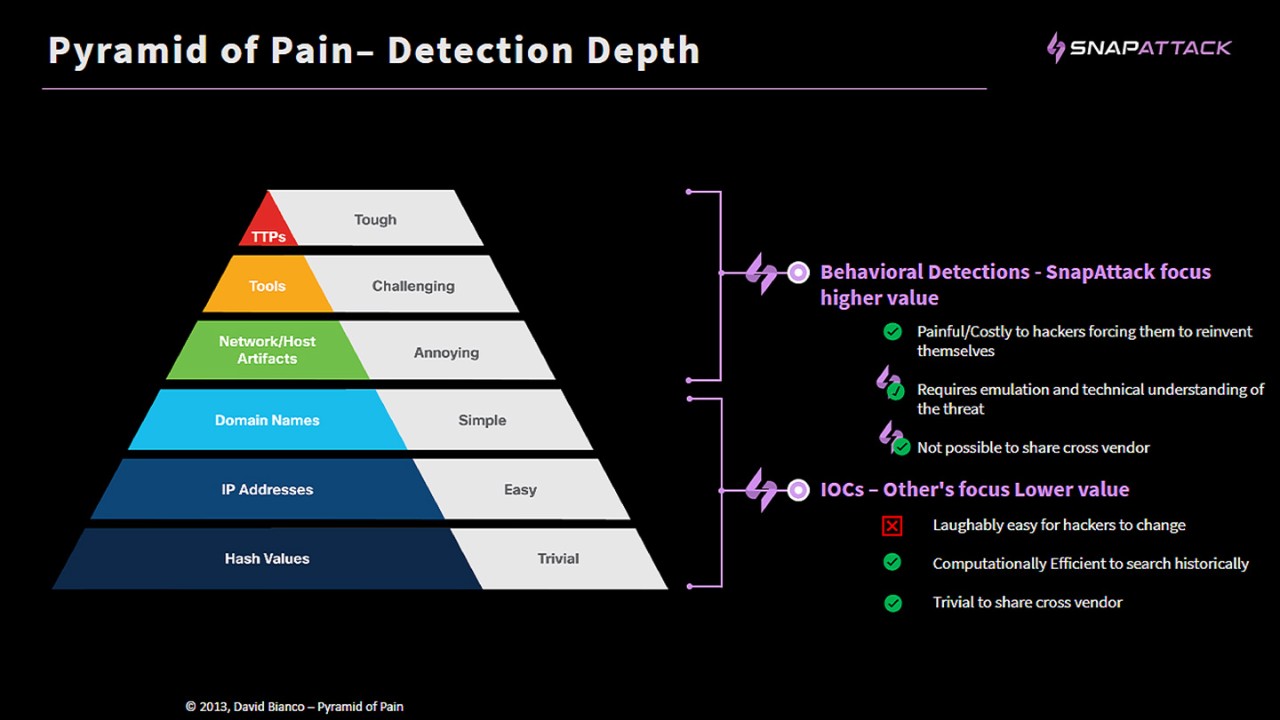
Our partnership with SnapAttack provides public sector organizations with a unique platform that combines threat intelligence, adversary emulation, detection engineering, threat hunting, and purple teaming—all to help them stay ahead of cyber threats and stop attacks before they occur. This all-in-one technology enables enterprises to get more from the tech they already own and more from the teams they already have.
SnapAttack was born from Booz Allen’s DarkLabs—a venture capital-style research and prototyping unit focused on national cybersecurity. In 2021, SnapAttack became a standalone company. Now, through our strategic partnership, we equip federal clients with collaborative, efficient, and robust threat-detection capabilities, technology, and services. We help their security teams achieve better outcomes, overcome barriers to information sharing, and improve visibility and efficiency across all hunt and detection capabilities.