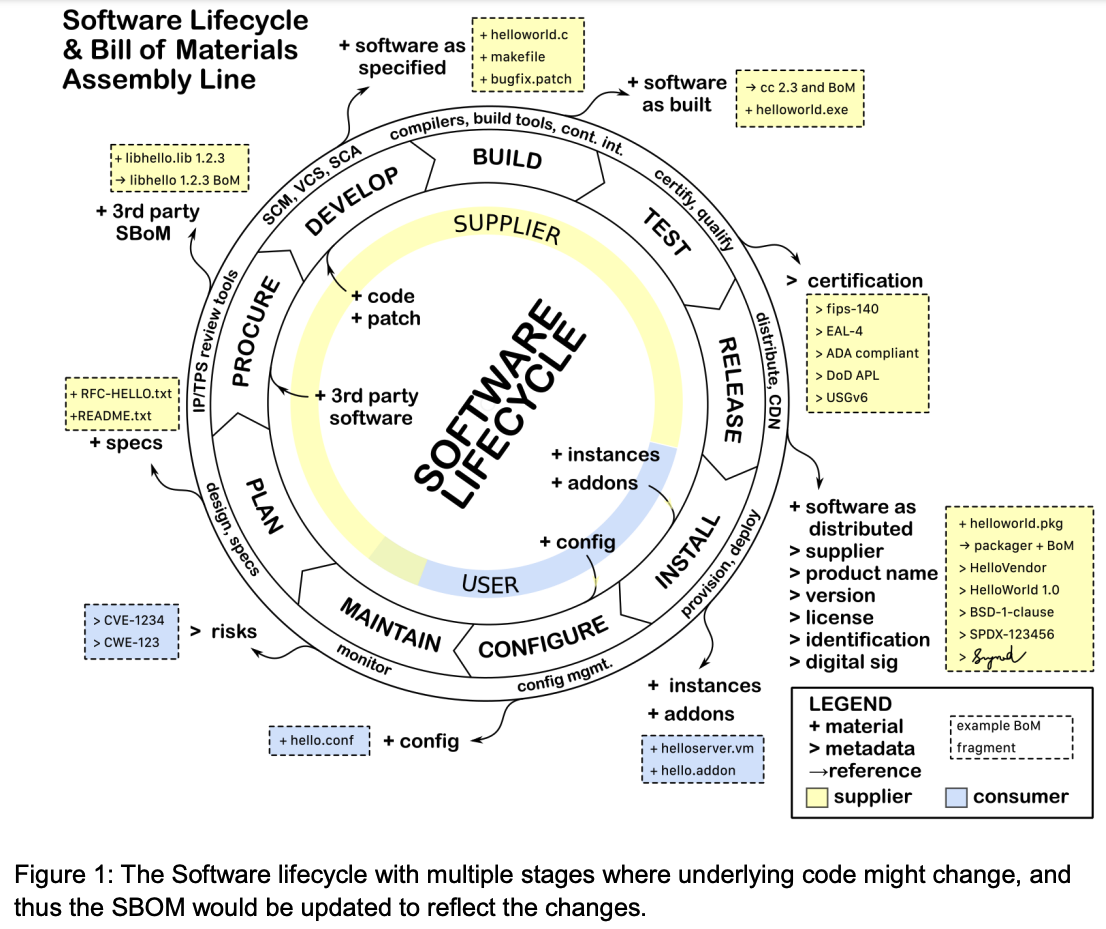
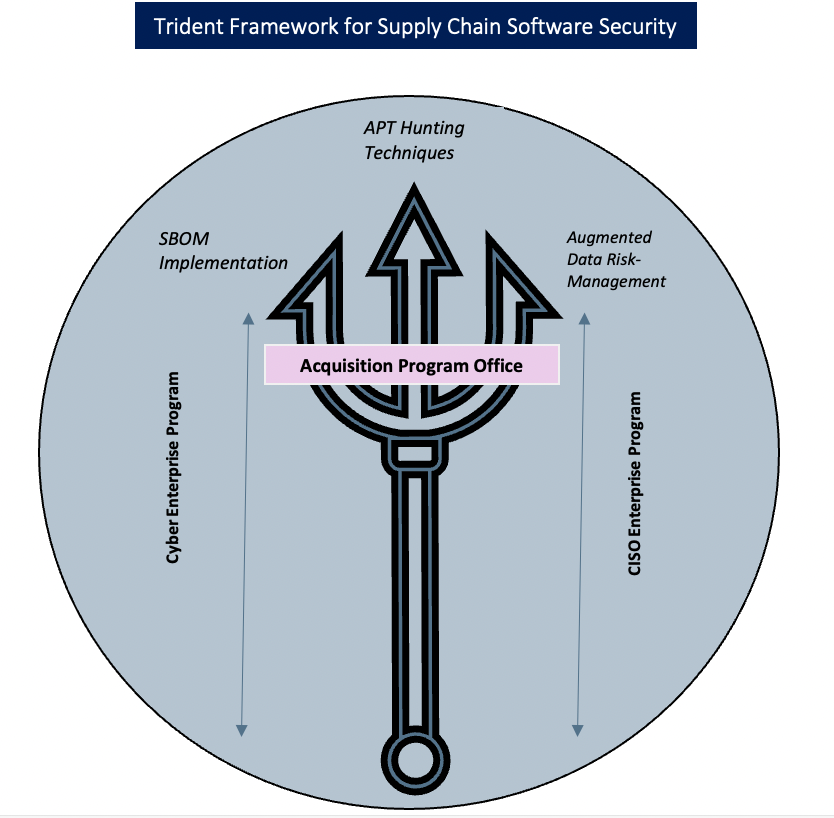
In an increasingly interconnected world, supply chain attacks can compromise a wide range of organizations in one swift hit. The SolarWinds attack and the Log4Shell vulnerability showed that such threats can profoundly harm national and economic security. No agency or company is immune. But your organization can proactively mitigate supply chain risks with commonly used tactics and techniques. In this post, we’ll discuss how a concept championed in the Biden administration’s cybersecurity executive order—the software bill of materials (SBOM)—can accelerate your risk mitigation efforts.
Now, SBOM is a relatively new term, and it sounds explosive when it rolls off the tongue. Said in passing in a national-defense setting, it could be mistaken for a new munition. In fact, an SBOM is more like an itemized receipt for software—or, if you are from the accounting world, a general ledger of software liabilities and assets. Now, that might not sound strong like a weapon, but think again. Implementing SBOMs in government and industry is a priority for national security. Understanding what SBOMs are, and why they are so important, can bring your organization one step closer to mitigating supply chain risks.