Our accelerators and packaged solutions blend leading-edge technological expertise with the highest quality user experience.
Accelerating Solution Innovations
Booz Allen offers a range of software platforms, analytical tools, and cybersecurity accelerators that seamlessly integrate today’s most advanced technology with bold thinking and unparalleled expertise. We specialize in designing intelligent, tailor-made solutions built to tackle the nation’s most critical missions.
Whether you’re looking to safeguard your AI systems against cyberattacks or harness and share real-time intelligence at the tactical edge, we have the tools, technology accelerators, and solutions to help you meet today’s challenges head-on. Working with us, you won’t just keep pace with the 21st century, you’ll take command of it. Please choose from the categories below to explore our offerings.
Featured Technology Accelerators
Mobile Security for the Future of Work
DISTRICT DEFEND®
To reduce security risks of classified data as devices are moved between facilities, we created District Defend, a software-based security platform that uses automated safeguards to defend organizations against threats. The result is safe local storage and a secure connection to approved networks.


The Future of Advanced Military Operations
MODULAR DETACHMENT KIT (MDK)
Our Modular Detachment Kit revolutionizes tactical command and control (C2), offering unprecedented multidomain integration. Bridging the technological gap, MDK introduces a modular, tailored mobile approach that provides warfighters with a clear understanding of the battlespace.
See Our Technology Accelerators in Action
Empowering Missions at Scale
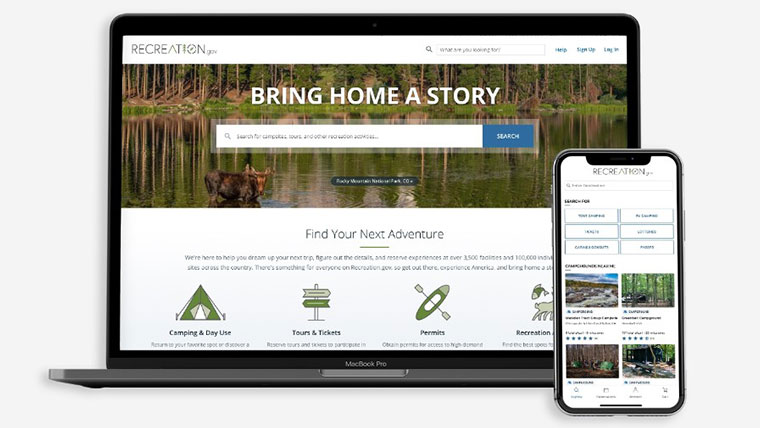
RECREATION.GOV
Working closely with stakeholders, we reinvented Recreation.gov by building a modern, scalable, cloud-native, e-commerce platform transforming how millions of visitors discover public lands. The new site is a one-stop shop for trip information, planning, and reservations from coast to coast.
Interested in Learning More About Booz Allen Technology Accelerators?
Subscribe to our newsletter for the latest insights, thought leadership, and analysis.