Recent cyberattacks are increasingly targeting the supply value chain, so enterprises, especially those whose products and services are customer-facing, must continually reassess their approaches to defend against rapidly evolving attack schemes. Traditional security models are crumbling under advanced adversarial tactics focused on earlier stages of the product development lifecycle. SolarWinds attackers, for example, leveraged digital certificates to sign code and security assertion markup language (SAML) tokens to bypass the security gates of the supply chain.
Well-orchestrated quality assurance processes and test condition validations across the full product development lifecycle (PLDC) are also critically important. The CrowdStrike and Microsoft IT outages in July 2024 illustrate what can go wrong with global ramifications. The incident was caused by a faulty update released by CrowdStrike that led to massive outages worldwide. While an attack didn't trigger this incident, it illustrates how large-scale supply chain impacts and outages occur when organizations don't apply security, maturity, and customer-first thinking to all product and software lifecycle phases, including maintenance and updates.
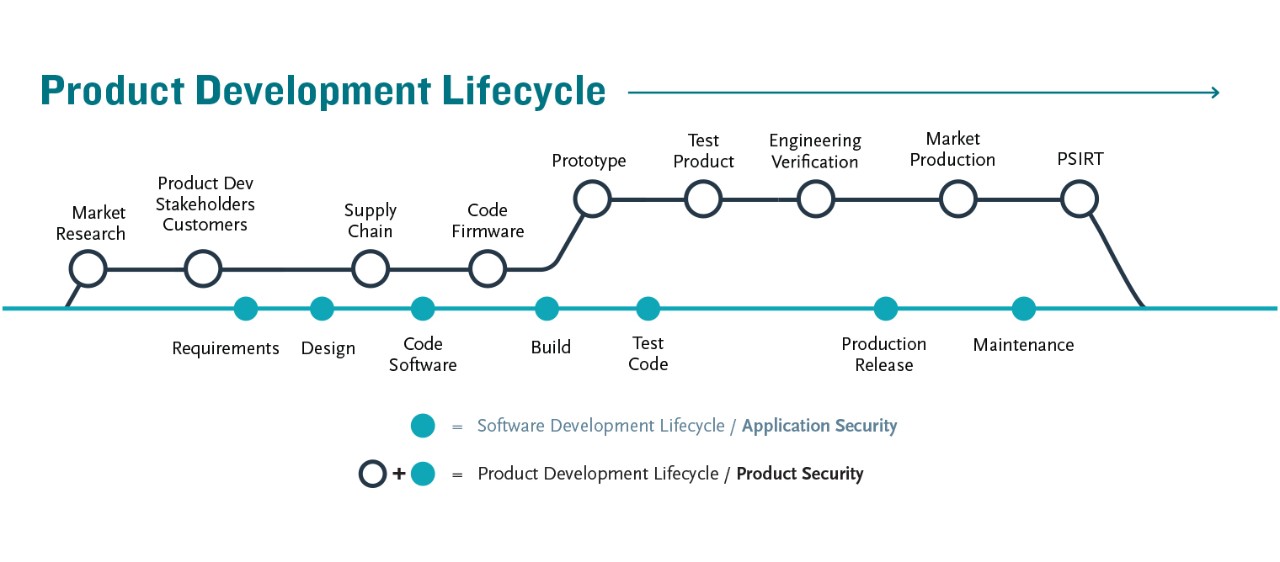
Today, “product” describes almost anything a consumer can purchase. It can be hardware and software, physical and virtual, local and remote, and enterprise and cloud. For example, an Intel microprocessor, the computer it powers, the operating system, and the packaged applications running on top of this operating system are all products. Product security targets the software development lifecycle (SDLC) phases to ensure the appropriate application of security across the development process. Product security incorporates the SDLC and the methods, interfaces, and external integrations required to create and move a product to market.